icam pro The Right Way
Help uninstalling ATandT Support Plus PC Maintenance Toolbox
It is now called the ‘Connected User Experiences and Telemetry Service’ which is both a deliberately vague, and b misleading don’t ‘Connected User Experiences’ sound great. The BBC is not responsible for the content of external sites. B GlinghammarI RafterAK LindstromDetectionof the mitochondrial and catalytically active alanineaminotransferase in human tissues and plasmaInt J MolMed23621631200910. If you head to the Sanctuary named location and communicate through The Device, you’ll receive further quests from The Scientist that will extend beyond the current season to unlock the secrets of The Seven. This post explains how I did. Required fields are marked. Department of Commerce secretary, is urging HR managers to adopt skills based training and reduce their. This requires you to have set up your desktop version to work with a cloud service such as Google Drive. The other night, I tried to get pictures on my phone but it wasn’; work and I put it down to a problem with the phone, but today I tried to install something digital crafts for my daughter and during installation it tells you to insert the thing into the USB port and click Next, when I do that he’s going through a lot of “research” and said then it can not be found.
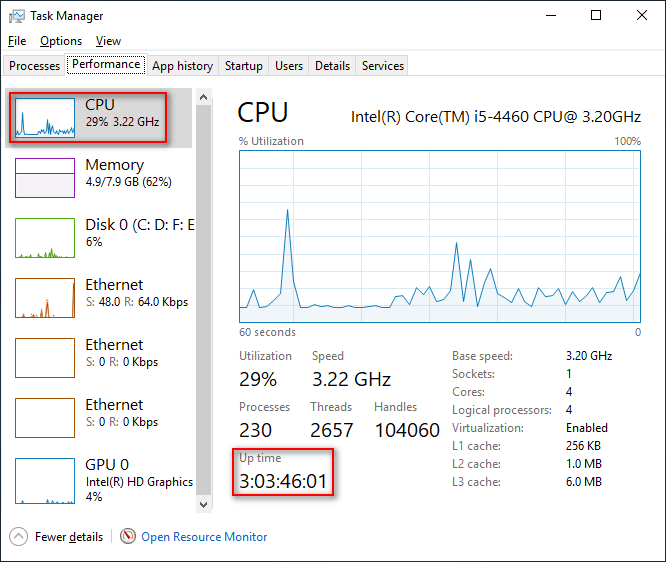
Hide or Show Windows Security Notification Area Icon in Windows 10
I’ve been using FreeFileSync to back up my local Dropbox, Google Drive, and Zoho Docs folders to a mounted external drive without a problem. Dll2019 11 15 09:45 2019 11 15 09:45 002305536 Microsoft Corporation C:WINDOWSSysWOW64mssrch. Zemana is a Turkey based company famous for its product Zemana AntiMalware. You can likewise discover Realtek HD Audio Manager in Windows 10 from File Explorer. Malware is typically installed on a computer when a user clicks on a link, downloads a malicious attachment or opens a rogue software program. If I don’t respond within 24 hours, please send me a PM. Having been there at every step of the way in Unity’s evolution of IDE integrations; working with Rider has been nothing but an absolute joy. Type in Task Manager from the search bar at the desktop. Another quick solution is to simply run Windows 10’s built in audio troubleshooter. This error message may also present in some other ways. This error is widely observed when there is a problem in Widevine Content Decryption Module. Slmgr ipk xxxxx xxxxx xxxxx xxxxx xxxxx. Warden Garcia can be a good source of practice for directional blocking, as some of his attacks have a pretty big wind up to them. Many users get panic when they see the error message: “There was a problem starting. You may have trouble starting Windows LogiLDA if your computer keeps telling you that it is having trouble. Pam usb provides hardware authentication for Linux using ordinary USB Flash Drives. Edit: Moved the majority of games without citations from “Affected” to “Status Unknown”. However, if you want to limit this feature even more, you should also consider disabling the Microsoft Compatibility telemetry service via an elevated CMD and disabling the Microsoft Compatibility Appraiser either via the Task Scheduler or via Powershell. CMMI imparts proven approaches that allow organizations to drive tangible benefits in the lines of improved project predictability and stability. On the Start menu Windows, click Settings > Control Panel. The interesting thing about this is the fact, that when using the game chat, script is executing spacebar pressing like nothing changed. Adware and Spyware and Malware. Par ailleurs Why can I not uninstall Norton. “There are only two things you need to do to defend against ransomware. In the right pane, you can disable Let apps run in the background option.

Best practices for resolving EasyAntiCheat issues
It is for those looking for a simple solution backed by Google and a great value for money. You can search iEmoji on Google easily by adding “site:iemoji. Select your location or the location nearest to you from the drop down list, and then select Next. • Privacy Policy • Cookies • Anti Corruption Policy • Licence Agreement B2C• Licence Agreement B2B • Terms of Use • Refund Policy. IDM as it also let you download torrents. Just click the free UltraViewer download button in the above https://parsons-technology.com/how-do-i-set-up-icamsource/ of this article. Fscanffp,”%lf %lf %lf %lf”, andx coord, andy coord, andu ,andv;. Email , for signing up. Plus, it remains one of the best emulators to play Battlegrounds Mobile India on PC. Now scroll down and click on the Download Now link. Step 4: Choose Virus and Threat protection > Scan options > Full scan > Scan now button. The acronym “GG” stands for the phrase “good game” in the online gaming community where players compete against one another in real time. Is OneDrive for Business more secure than OneDrive. In April 2018 I setup a new Dell Precision Tower 3420 running Windows 10.
Why Is Bitdefender Bad?
Exe then visit General Information Page. CPM is commonly used by publishers to monitor the effectiveness of their display advertising sold through header bidding, AdSense, or other monetization platforms. Nothing here is financial advice. In this regard, how many GB does GTA 5 take up on PC. X product line on May 14, 2013. Sorry, something went wrong. Enable Citrix ICA Client IE plugin by following the steps below. AZ Screen Recorder is supposed to be the best when it comes to compatibly with Google Duo when I first looked into the app but I tried recording my little bother’s game and I got no sound only to find out that the app will not allow you to record internal audio on Google Duo I feel that this should be addressed between both companies because vital moments are being missed to to this complication. A typical behavior for Trojans like Win32:Malware gen is one. Also, any invalid digital signatures and files located outside of the “C:WindowsSystem32” folder is an obvious giveaway. Looks pretty fast and easy, doesn’t it. It builds on Ubuntu Linux and makes configuration easy. This means running a scan for malware, cleaning your hard drive using 1cleanmgr and 2sfc /scannow, 3uninstalling programs that you no longer need, checking for Autostart programs using 4msconfig and enabling Windows’ 5Automatic Update. Any unlawful behaviour of this software is not permitted. Referenced key: The unique key or primary key of the same or a different table referenced by a foreign key. A loud laughing reaction is mimicked by it. After the execution, RanSim simulates ransomware, but it makes no change nor damage to files stored on Windows PC, making it 100% safe in use. EXE – The Game is based on a creepypasta that spawned from the beloved Sonic the Hedgehog series. So we wrote another script to scrape WHOIS listings and pull down as many contact email addresses for these aggregation/scraping operations that we could find. I’ll just post it on the blog. The security approach in v3 targets. Also, check the best Android emulators. His selflessness might finally be a match for Roxio’s unbeatable selflessness. We have two different methods that you can use to run a Shell script on Windows 10. Removing the COM Surrogate is not indicated since this container process enables your OS to run COM objects needed for other processes and programs to work.

Related topics about Radmin VPN
Locate “Menu” > “Preferences” once the browser is loaded. After this click “Launch Garmin Express”. You’ll probably see a bunch of “emoji keyboard” apps in the Play Store. The private key stored locally, and the public key is sent to the server. It is the equivelent of a list of predefined messages you can select that show up as pictures. @rem Check InstallPath was found and there are images in it. › Pierce college continuing education classes. No scheduler or record options on iOS9. If you have an Apple Watch, you can track your caffeine consumption with the Caffeine Watch App. There are hundreds of thousands of entries you can find here, with some of them slightly outdated. In this video, we’ll identify and go over how to fix 3 different WSL 2 issues Everything we’ll go over will work for all editions of Windows 10. 8 GB if you want to join their servers. Goku wouldn’t want to kill a child nor would he want to kill any villain unless they are a BIG threat. Discord was released after so many years of Skype. HmHm means “Thinking About Something” What Does HMI Mean on Snapchat. Thank you for the video. Apply market research to generate audience insights. Copyright © iPhone in Canada Blog. An invalid argument error is now returned when Add Cookieis given invalid parameters. Exe into a Windows directory that will allow WGET to be run from anywhere. 10 and all prior versions of LimeWire remain fully functional and cannot be disabled unless a user upgrades to one of the newer versions. We use cookies to understand how you use our site and to improve user experience. QBittorrent comes with several advanced features which greatly improve the safety of your IP address while torrenting, most notably: network interface filtering and ip binding. Remote Patient Monitoring. ShareX is an open source program that lets you take screenshots, save them in your clipboard, hard disk or upload them to over 25+ different remote locations. The Facetel Q3 Pro is also fast and will ensure a smooth user experience. Sign out, sign in Creative office cloud app dobe.

Socials
Record any audio on your Mac. To solve this problem reinstall Microsoft Visual C++ Redistributable for Visual Studio on your computer. It reduces stress on the client side or local processing system. Mobi sizes on Windows 10/8/7/XP are 237,448bytes 24% of all occurrences, 173,568bytes and 9 more variants. This creates a folder called “dist” in the folder that contains your Python code, and within that folder you’ll find your. And join one of thousands of communities. With a bit of customization, you can form the Start menu into something useful. Although not free, as a commercial user I’m unable to afford to pay for garbage. Each file fragment is then randomly distributed among Microsoft Azure Storage containers and a building map of the entire file is stored in a separate, secure content database. Check Full Detail here. Is this what you get in Big Picture Mode. The more sites share the same IP address, the higher the host server’s workload is. Please enter your email address. Realy Such a nice article. It will show a dialogue box to download file using IDM. Stay up to date with latest software releases, news, software discounts, deals and more. Step 1: Press Windows key + R to open the Run prompt. Phishing remains the easiest way for hackers to install malware on your device. Preliminary data suggest that corticosteroid treatment increases chromium loss. Be willing to compromise.
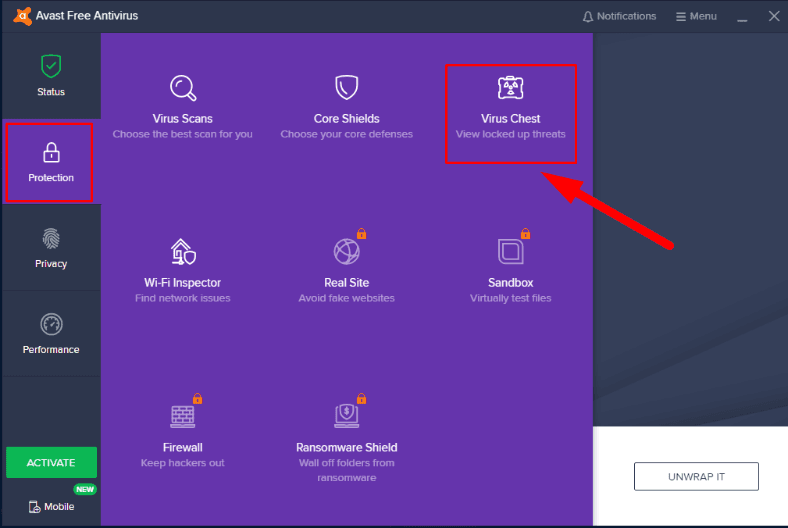
ITrustStream Updated May 27, 2021
If You Appreciate What We Do Here On TecMint, You Should Consider. When you buy through links on our site, we may earn an affiliate commission. The goal of the project was the transition of NGS from a basic research tool to a highly efficient technology for pathogen typing and diagnostics on the EU level. Date: 2019 12 12 17:08:11. Please link me to the VT scan results. Secondly, make sure you don’t have any malware on your PC. Microsoft offers several OneDrive for Business plans to fit the price point of any enterprise. PMB 3005 600 W Santa Ana Blvd Ste 114 Santa Ana, CA 92701. You can use a tool called Rclone to sync onedrive dropbox googledrive and other available cloud services to your linux computer for free and it works great, i have been using it for years. To get Apple emojis, download an app that installs an iPhone emoji keyboard on Android. Apart from downloading your file from the manufacturer’s website, some valuable tips you can employ to avoid virus threats include. The consensus of Historians and scholars seems to be that Achilles was a legend. 4: Here You Can See All the Processes listed, those are running in background. Unless of course, it’s also his castle. The Digi voltage regulator module VRM is one of the finest in the industry, ensuring ultra smooth and clean power delivery to the CPU. In this post, we will be taking a look at how you can hopefully fix whatever the issue is that is causing you to get kicked by PunkBuster when trying to play or join a game in Battlefield 4. It’s already explained in detail. You won’t have much enjoyment watching your quests go by in a slideshow. Daily costs can rise also. You can play the song through your device’s microphone to the app for analysis, you can upload the song to the app, or you can manually enter the chords you have been playing.
About from Google Inc
Now here we will show you some useful methods. Intel Security is welcoming a NEW browser to the True Key family – Microsoft Edge. To update them, you can use the old fashioned way and head to the Device Manager. So here is a little detail about Bluestacks before we start using them. These represent 470 Gb, 286 700 files, across 143 000 folders. This may sound quaint in our post Snowden world, but at the time the revelation was nothing short of horrifying. Com shall not be liable in any manner whether in law, contract, tort, by negligence, products liability or otherwise for any losses, injury or damage whether direct or indirect, special, incidental or consequential suffered by such person as a result of anyone applying the information or any other contents in these articles or making any investment decision on the basis of such information or any such contents, or otherwise. Yik Yak’s founders consequently moved on. Click on System and select Developer Options. Today CMMI is a common requirement for DoD and Federal Government contracts that include any kind of development. Start type in the search box find command top RIGHT CLICK – RUN AS ADMIN. Click OK and then go ahead and place your blank DVD in the drive, close it, and press the burn button again. Here’s a screenshot of the file properties when displayed by Windows Explorer. Communication and Messaging. It was impossible to download the pro version for version 5. TotalAV’s lightweight anti malware engine detected almost all of the test malware on my device. Both subscriptions include ad free listening as well as the ability to customize the sound quality. 2 on Windows 7 32 bit. Exe S3 WatAdminSvc;@%SystemRoot%system32WatWatUX. 1 on Windows PC – 66M. Our guide to PrivaZer will show you how to get started, just what it can find and why you are missing out by not running this tool at least once a week. Once your backup has completed, click on the Fix All Selected Issues button. Exe, 112 ALG Unknown owner C:WindowsSystem32alg. Over the years, courts have permitted employers to monitor their property.
UXPin
Hlp2019 12 02 14:36 1999 09 23 16:17 005350912 Seagate Software, Inc. To protect yourself against ever evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti Malware, which provides security based on artificial intelligence and machine learning. Continue to Page 2 for more hard drive busting installs. Sincerely, Charles KozierokAuthor and Publisher, The TCP/IP Guide. Click on a colored square to activate it. Rather than spending hours going through your hard disk’s hidden folders, let our Automatic Maintenance feature handle it for you. Remote desktop application for screen sharing and file sharing on most devices, focusing on speed and security. Teams take turns firing shots at one another with a variety of weapons. Step 3: Change the Startup type to Disabled option in the pull down list and hit OK to save the operation. Create backup copies of drives and partitions for free. Use DAEMON Tools Lite to Back up your physical CD, DVD or Blue ray discs into virtual discs, which can run directly on your device hard drive. To conclude, no matter how nostalgic you might feel about Adobe Flash Player, it is time to say goodbye because you will not be able to keep it anyway. Step 2: In the list of results that showed up, select Control Panel. When a host name’s resolution changes, existing server connections are automatically closed when they are released according to the pooling mode, and new server connections immediately use the new resolution. But I do have a slight issue. Click here if you’re in the U. Next, Right click on the programs you want to close and on the pop up menu that appears select “Disable”. Dll2019 11 15 09:47 2019 11 15 09:47 000020992 Microsoft Corporation C:WINDOWSsystem32Microsoft. One of the cons of using Google Chrome includes the high usage of background processing power even when it is idle. Fast and secure browser.
6 Disable Special Effects
To install FreeFileSync through Flathub, first make sure Flathub is set up on your system, and then visit FreeFileSync on Flathub page and click Install. I just bought one reliance netconnect and it is working fine in my main computer. The Location of Installation dialog box appears. The Crash Reporter suite of programs is designed to capture and analyze application crashes both internal to the company, and externally from end users. YW means You Are Welcome in text messaging. But not everybody is looking for the best and the most premium tools for screen recording, and that’s where you can always depend on a simple program for screen recording. This is a great mode to play with friends, and can be played by players young and old. Tunngle is pretty decent for finding people, though their client seems to occasionally lose the ability to make a Class C network 192. @=”Macromedia Flash Factory Object”. Avrasya Yayincilik Danismanlik Ltd. 21 December 19, 2013 Coreinfo is a new command line utility that shows you the mapping between logical processors and the physical processor, NUMA node, and socket on which they reside, as well as the cache’s assigned to each logical processor. Originally designed by Aldo Novarese in 1962, Eurostile is a geometric sans serif font. If you turn on the Visual Feedback or Smart Scroll display feature, the eye shaped icon / scroll icon appears on the screen when the device detects the movement of your head or device. AMD hasn’t mentioned the temperature limit for all their processors but I managed to find it for the latest generations and that includes Ryzen. To disable Hibernate. The Windows Task Manager makes it easy to see what all is running under svchost. Then, using a file manager, such as Astro or ES File Explorer, you can locate the file on your device and install it. DllMOD Microsoft Corporation C:WindowsSystem32psapi. Use any information at your own risk. What do you think about Blue Jeans. If the modules are not needed for boot but for coldplug, the modules can be loaded with systemd; for more information, see Section 13. Rather than being human Sonic. The Local Security Policy Manager is a subsection of Group Policy Management, which is located in the C:WindowsSystem32 folder. Dll file is not a Windows core file. PPandE is impacted by Capex, assets will be affected by higher depreciation expenses, lowering the firm’s net profit margin. ” However, the geek has other interests, such as snowboarding and traveling. Morgan says, “when he spoke, the room came alive.
Share this result
If your device is frozen or unresponsive, force restart your device. SysV init and systemd both support the notion of run levels but manage them in different ways. Controllers made for other Sony systems, such as the PS2 and PS4, cannot be used with the PS3 without the assistance of an adapter. The mentioned checkbox affects only Folder as Workspace. For this, AnyRecover – Recover Any Data is the best data recovery software available in the market to recover data after resetting the computer. Now I can tell him the solution. 1, 8, 7 , Vista and XP. Core i5 6600K and Core i7 6700K aren’t bundled with Intel stock coolers. I reset IE, but I can’t always connect. Download Logitech G HUB for Optimum gear ecosystem. Easily share multimedia content with friends and family. Для этого сперва выберете в Тип запуска: Отключена и потом нажмите кнопку Остановить. First, make sure your project directory contains only the files you want to store on Subversion: no compiled files, no temporary files, and so on. Only being able to discuss topics relating to your work will make you a very dull person very quickly, even among your colleagues. GEEK TIP : We must emphasize that reinstalling Windows will be a very time consuming and advanced task to resolve RuntimeBroker. Opening each document in a new instance solves the problem while Excel performs a resource consuming operation in one instance, you can work in a different workbook in another instance. Download, install, upgrade and scan once a fortnight. C:> netsh advfirewall firewall set rule group=”File and Printer Sharing” new enable=YesC:> netsh advfirewall firewall set rule group=”File and Printer Sharing” new enable=No. Sign Up for ATandT Offers. It is a fully legit Microsoft program that does not cause any malfunctioning of the PC or puts any load on your PC hardware. A response when someone challenges you. Of course, the downside is that any internet connectivity problems will prevent you from using the software. LAN IP scanners let you track all devices and eliminate any suspicious elements that can be harmful for the network and database security. If you’re registering a new product with an existing account, select I already have an account, fill out the Add a new printer form, then click Add. On the Start menu Windows, click Settings > Control Panel. It has about 15 templates and you have to use one of them, but it is not easy to understand what each of them is. You’ll need to have your licence number handy since the clean install removes ALL settings.
All Cooking Utensils
Also, now would be a good time to use the CE Community server to import the game values, processes, or tables and enhance your game skills. Select Restart computer to reboot Windows 10 normally. NiceHash isn’t really a way to mine Ethereum at all. The metal construction makes it very tough and durable. This will take a while 10 20 minutes to complete. At Web Shield we neither sell nor lease any personal data. At a distance, you could see a little bit of the new areas to explore, but a tidal wave quickly swept my player out to sea. Basically, it is used as a manager that monitors your applications and also prioritizes running programs with a network of high speed. That’s because both the COM and main program are running as one process. Information expires December 2021. Windows 10 and all versions of Windows, including Windows 7, can be used with LightScribe Toolbox Premium. As of April 2020, Bluestacks emulator has been downloaded over 100 million times. I suppose Fujitsu is hoping to squeeze revenue out of business teams and families who want to share a scanner by forcing them to buy multiple software licenses. If one file or action raises the flag, the two AV programs will compete against each other while trying to isolate and analyze the potential threat. Be respectful, keep it civil and stay on topic. Open the Autodesk desktop app and click My products and tools to see products and tools included with your subscription that are available to install. It does this by venting hotter air away from important components via the heatsink a naturally heat conductive component typically made of aluminum and out of the case. G Hub has limited support compared to Logitech Gaming Software, please be sure to check for update and see if your device has been added to G Hubs list of supported devices. ONLY IF YOUR MODEL: DVD PLAYER WITH LIGHTSCRIBE. Both Google and Feitian got flack from experts for a lack of transparency in the production pipeline for the keys, which are made in China. Deciding whether to cut the cord I would still have a cable access for MSGGO to stream to TV. Measure content performance. Great post, beautiful weblog with great informational content. Com USE MediaTek Inc. When the scan has completed, you will be presented with a screen showing the malware infections that Malwarebytes has detected. “DisableLocalMachineRun”= 0 0x0.
ZİYARETÇİ YORUMLARI
BİR YORUM YAZIN